How To Spot A Fake Email [2023]: 7 Ways To Recognize A Threat in The Digital Era
Written by, Sandeep Kumar
Updated March, 14, 2023
Written by, Sandeep Kumar
Updated March, 14, 2023
We’re aware of the dangers such as email scams and phishing attempts.
But do we know how to spot a fake email?
It’s not always easy, particularly if the scammer is good at mimicking a legitimate message.
In this article, we’ll look at some key indicators that can help you tell whether an email is genuine or not. We’ll also discuss the potential risks associated with falling for a phishing scam.
Read on and stay safe online!
Phishing isn’t the only hack or digital threat out there. But, it’s undoubtedly the one most often connected with your emails.
Though many legitimate email providers have been struggling and effectively eliminating this common threat (by sending such messages in the spam folder), some might also successfully land in your inbox.
This is precisely what makes phishing emails more dangerous. Moreover, most of us recklessly click on emails from unknown senders, hoping for a job offer or some tempting reward.
You know how real-time HRs, CEOs, recruiting teams, etc., have this included in their email? Well, hackers usually take advantage of this stuff. So, the first trick to learn is to avoid this.
Hackers are masters of creating and mimicking an almost identical email address to lure you into their phishing attack. They are NEVER registered to the original domain that most official and serious companies have.
For example, each legitimate business/ company usually buys their own domain (what comes after the @ in an email address) since they’re not such an expensive asset for a business.
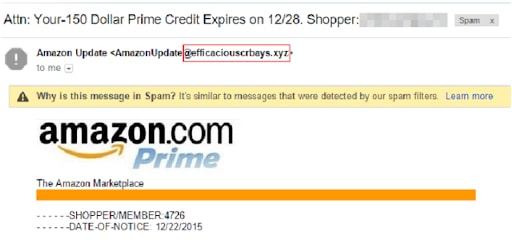
Some hackers are much brighter than the example mentioned above – they aren’t that cheap.
Instead, they invest in similar domains that might trick your mind into thinking that ‘you’ just read an almost identical domain as the legit one. And you might just not figure out that those are two different domains.
Here are some examples, or if we may refer to them as ‘the domain doppelgangers:’
| Original Domain | Doppelganger Domain |
| netflix.com | netffix.com |
| kaspersky.com | kapersky.com |
| uralairlines.ru | uralairilnes.com |
| cofense.com | confense.com |
| apple.com | applee.com |
| Ebay.com | ebaysupport.com |
NOTE: If someone’s using a lookalike domain for criminal activity (phishing), it’s essential to report it. This can help prevent others from falling victim to the same scam.
For a more secure online browsing, you can turn either to Google Safe Browsing or Netcraft.
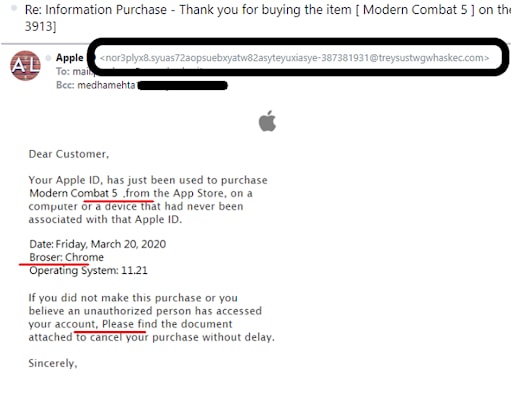
A legit business/company already has your credentials – especially your first name. Thus, spotting “dear customer,” “dear client,” ‘dear valued member,’ or alike should be a big red flag.
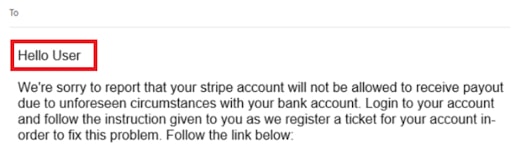
Pushy is the common language of marketers. But, sometimes hackers use this language to hide an ‘intriguing marketing or product offer.’
The urgent tone is most often an additional disguise with a phony bank email domain, asking for an urgent reaction for you to secure your money, like stop a big buck payment from your account, claim an award, etc.
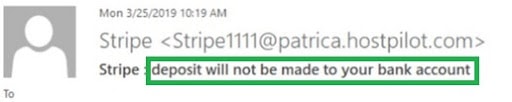
Hackers and phisher-men know how to trigger your attention and your reaction. Therefore, beware of this extremely sensitive emotional field they’re playing.
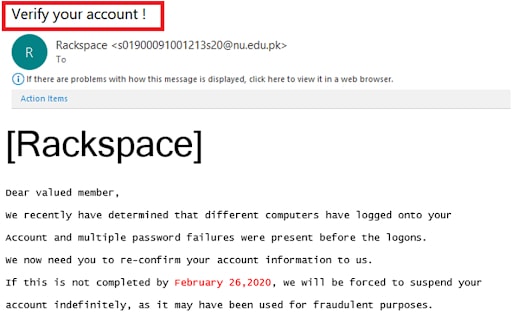
The Bcc field stands for ‘blind carbon copy.’ It is usually used to keep other recipients from seeing the personal information and email addresses — even though they’re receiving the same information.
There’s nothing wrong with this approach. And, still, when a bank reaches out for transaction confirmation or other sensitive personal info, they will NOT include you in the Bcc field. Think about it.
There’s allegedly something wrong with your account – how come the same thing is happening to others?
Spoiler Alert! It’s obviously a fake email containing an attempt of a phishing attack.
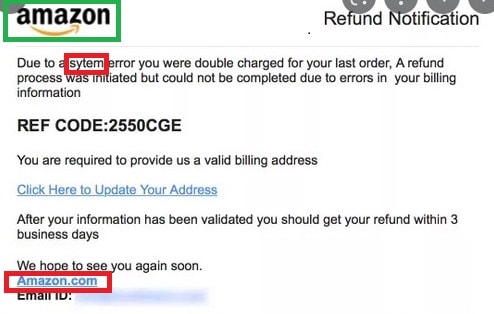
Though, notice the smart and sneaky usage of the official amazon.com logo – an easy-to-fall in trap.
How to do this?
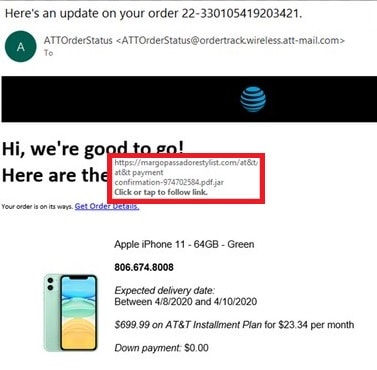
You should reduce the threat a notch as soon as you notice that your account might be at risk. If the URL link is hidden correctly in a notice or a message: ‘follow this document’s instruction for further details.’ Or, ‘follow this link to change your password.’
Here’s a trick for it:
When you put your mouse pointer over a link, the actual web address will appear in a bar at the bottom of your screen.
This is what the link does when you click on it (without the consequences of actually clicking on it).
If the website address that pops up differs from the one in the text or doesn’t start with https://, it’s a fake and malicious email.
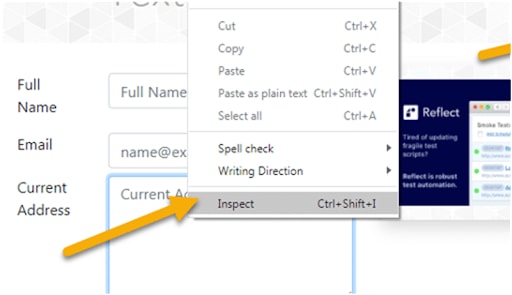
By doing this, a new screen will pop up on the bottom, or the right side, showing the code of the email.
Be on the lookout for the text following the <a href=(text). This text shows the exact URL and where it’ll take you after clicking the link.
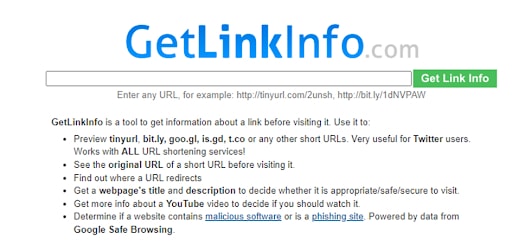
This website provides info on how to obtain information about links and URLs that have been shortened.
Legit companies follow strict procedures and editorial standards, so punctuation, grammatical, and even spelling errors are a screaming red flag!
Do you really think that a highly reputable and world-leading company like Apple would allow themselves to press ‘Send’ on an email such as this one
Let’s assume that you’re sure the email you received is fraudulent, fake, and malicious intent. What to do next?
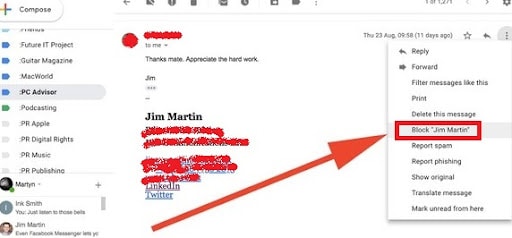
Blocking the sender will prevent your account from receiving further malicious emails from that specific sender.
However, blocking a sender is done differently by various email providers. Still, it is usually done by clicking on ‘More’ or the three dots in the corner – after clicking on the email, you wish to report.
Then, a falling menu appears with many options, and you choose ‘block sender.’
This is a Gmail example:
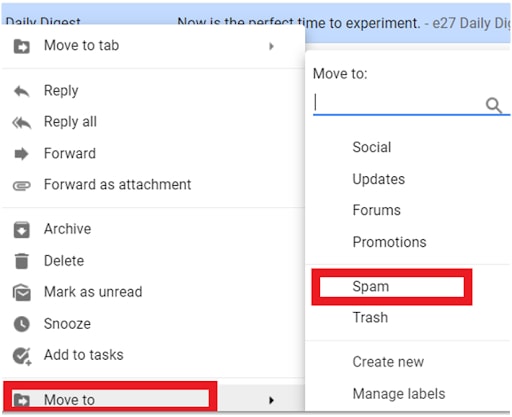
If you’re positive the email is fake, you may proceed to this step without opening the email.
Just right-click the email from your inbox, click on ‘Move to’ – and select ‘Spam.’
If the phishing email is received from someone posing as a company, you should first forward the email to the original company.
You should find their official customer service email address (usually on their official site), so they can be aware of this.
Afterward, proceed with reporting them to one of the following organizations:
So, how can you tell if an email is real?
The answer isn’t as simple as you think. However, by being aware of the signs pointing to a fake email and taking a few precautions – you can help protect yourself from becoming a victim of cybercrime.
Remember always to be vigilant when opening emails, especially those that seem suspicious.
Furthermore, if you’re ever in doubt about the legitimacy of an email, don’t hesitate to reach out for help.