How To Hack Someone’s Email (2023): Tips and Tricks to Breach Security and Keep Your Account Safe
Written by, Sandeep Kumar
Updated March, 14, 2023
Written by, Sandeep Kumar
Updated March, 14, 2023
Just because email is one of the oldest and most popular forms of online communication, it doesn’t mean it’s hack-proof.
That said, email accounts are some of the easiest to crack into, especially if you know some basic info about the person you’re targeting.
In this guide, you’ll read all about how to hack someone’s email account using simple techniques that anyone can perform.
Emails contain a lot of striking information that hackers might be intrigued by. For example, things like:
Thus, hackers found numerous versatile ways to breach an email.
Ever wonder how hackers always get inside an email, even though you have a strong password?
Thanks to this technique, called password guessing – and it’s easier than 1, 2, 3.
Here’s how it works:
Hackers gain access to one of your other online accounts – maybe an old forum account or an abandoned social media profile. The one that contains that relevant info for them. Once they have your login credentials for that account, they can use the “forgot password” feature on your original email account.
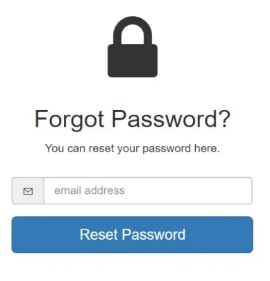
With a little trial and effort, they will eventually piece together your email password using the information from your other account.
So, the next time you choose a password, make sure it’s something truly unique and not just a different combination of something you’ve previously used. That way, even if a hacker gains access to one of your other accounts, they’ll still feel confused about crack-opening your email.
Hacking someone’s email is disturbingly easy – it requires a click on an infected link. And hackers use these links disguised as misusing a word, promotion, and an incredible offer, which further sparks the human curiosity and gullibility.
Hackers send an email posing as a legitimate person or a company, but when you click on the link – it takes you to a fake login website (which is difficult to be recognized and separate from the genuine ones). You’ll probably never guess you were scammed if you fall for these phishing links.
However, hackers are granted access by simply entering your email address and password on these sites. From there, anything can happen:
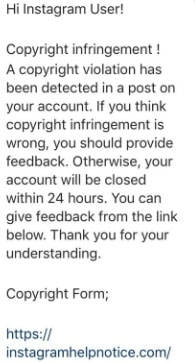
Email hacking is on the rise – and social engineering is one of the most popular methods used by hackers.
In a nutshell, email hacking involves tricking someone into disclosing information or taking an action that enables the hacker to gain access to their account.
For instance, a hacker might pose as a customer service representative and trick the victim into giving them their password. Or, they might send an email that appears to be from a trusted source (a bank or credit card company), including a link that downloads malware on the victim’s device.
Hackers can gain access to a second account that belongs to their initial cyber victim – one that’s linked to their email.
We’re talking about a situation where you’re asked to provide a secondary email address in case your original one (linked to a Google Account or your Facebook profile) gets hacked/ locked – to be able to retrieve your social accounts.
However, this ‘advanced opportunity’ can be turned against a user by using this secondary account. Why? Well, the password of the primary one can be reset easily, and thus, full access is enabled to all other accounts linked to the primary email address.
Wi-Fi’s are insecure networks – I bet you’ve already heard this.
Here’s how they work:
When connected to a public Wi-Fi network, you’re sharing that connection with anyone connected to the same network. This means that if someone on the same network is luring you to hack someone and has a tiny bit of knowledge of what they’re doing, your passwords are just waiting to be picked up and intercepted.
And, if YOU’re the predator – here are the basics to ‘get your prey:’
Username: “admin” (no quotations)
Password: “password” (no quotations)
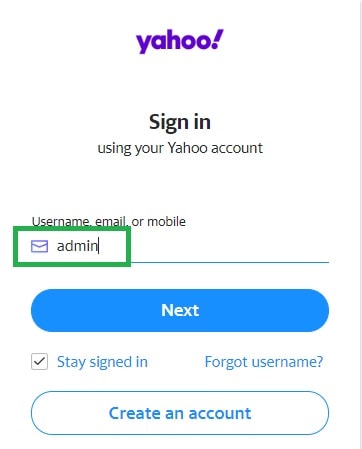
These are the primary login credentials for many router administration panels. Therefore, if someone hasn’t changed them – you’ll be able to log right in. Once there, – you can access ANY email account currently set up on that router.
Amazing, right?!
Note: These are the default login credentials for many router administration panels. So, when not changed, you can easily log right in.
Now, this is not a fully remote hack into someone’s email like the ones explained previously. So, to hack into someone’s email using this method in particular, you need access to their PC – or at least install a program that will further allow access to their desktop.
To do this, follow these next instructions:
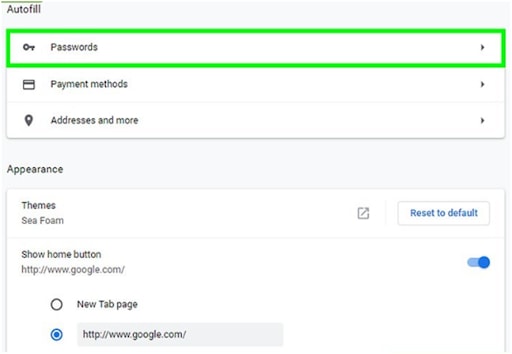
For example, if you’re aiming for a Gmail account, search for “google” or a Microsoft account – “outlook,” etc.
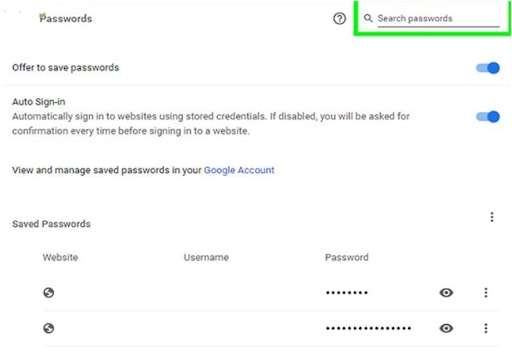
That’s it!
A ‘Keylogger’ is a program that identifies and records the keystrokes on the targeted device. You can reveal passwords and other important information about a user by doing this. A keylogger program is a ‘stealth program.’ The program is visible — otherwise, nobody would use their device to reveal information; thus, the entire concept of the existence of the keylogger program would be a total failure.
Here are some of the widely popular (free) programs to use:
With no further ado, here’s the procedure to follow and see how the Keyloggers program works when hacking someone’s email address and password.

After some time of using the ‘victim’s device,’ you should either be able to view their logs (which were directly sent to your email) or manually view the logs by clicking the log viewer from the same device. Or remotely if you have installed another software that allows you to enter their device remotely.
This is taking advantage of the two-factor authentication and ‘additional security’ implemented by most email providers worldwide.
Yes, you can hack someone’s email by knowing their phone number (you can get it from their friend or by asking them yourself). Sounds interesting?
Here’s how to do it:
For example, Google’s is [email protected].
There you have it, folks.
Breaking the myth that hacking is unimaginably complex. These ways prove that anyone could hack anybody’s email account with a bit of help and logic.
However, remember that hacking is a serious crime under the penalty law of the United States. Hence, you can expect severe consequences and some pretty hefty penalties if caught.
On the other hand, if you suspect that your email has been compromised, before taking any action, report it to an IT security company and to your email provider too.
And remember – while you’re out there luring your ‘victim,’ you’re someone else’s target.
Stay safe in the online world!